The Internet of Things (IoT) is a reality that changes several aspects of our daily life, from smart home monitoring to the management of critical infrastructure. The “Routing Protocol for low power and Lossy networks” (RPL) is the only de-facto standardized routing protocol in IoT networks and is thus deployed in environmental monitoring, healthcare, smart building, and many other IoT applications. In literature, we can find several attacks aiming to affect and disrupt RPL-based networks. Therefore, it is fundamental to develop security mechanisms that detect and mitigate any potential attack in RPL-based networks. Current state-of-the-art security solutions deal with very few attacks while introducing heavy mechanisms at the expense of IoT devices and the overall network performance.
In this work, we aim to develop an Intrusion Detection System (IDS) capable of dealing with multiple attacks while avoiding any RPL overhead. The proposed system is called DETONAR - DETector of rOutiNg Attacks in Rpl - and it relies on a packet sniffing approach. DETONAR uses a combination of signature and anomaly-based rules to identify any malicious behavior in the traffic (e.g., application and DIO packets). To the best of our knowledge, there are no exhaustive datasets containing RPL traffic for a vast range of attacks. To overcome this issue and evaluate our IDS, we propose RADAR - Routing Attacks DAtaset for Rpl: the dataset contains five simulations for each of the 14 considered attacks in 16 static-nodes networks. DETONAR’s attack detection exceeds 80% for 10 attacks out of 14, while maintaining false positives close to zero.
To the best of our knowledge, literature lacks of an exhaustive datasets containing RPL traffic for a vast range of known routing attacks. We aim at filling this lack by proposing RADAR. This dataset represents a novelty both in terms of the variety of considered routing attacks and extracted traffic. We use Netsim () to implement 14 well-known attacks against RPL. RADAR represents the most significant dataset for routing attacks in RPL. RADAR contains five simulations for each attack. The networks deployed for each simulation contains 16 IoT devices and a single border router belonging to a single DODAG structure. Moreover, RADAR contains ten legitimate simulations, useful for security systems setup and general traffic analysis.
RADAR is organized into subfolders of attacks scenarios. This means that RADAR contains one subfolder for each attack type that have been simulated, along with an additional subfolder containing legitimate simulations. RADAR contains five simulations for each attack subfolder. In RADAR, each simulation is represented by a single packet trace file (csv format) containing the list of packets exchanged during the simulation. Each of the packet trace files contains a list of all packets exchanged by any node throughout the simulation. These packets are not stored in raw format. Instead NetSim stores a set of features for each of the packets recorded. Available features are: packet type, application name, source, destination, transmitter and receiver identities, arrival and start time for application, network, data link, and physical layers and payload size for the same layers. Source, destination, gateway, and next-hop IP addresses are also recorded along with the rank and version values for RPL control packets. Along with the packet trace files, each attack subfolder contains a text file that stores the supposed attack start time. More details on this can be found in the official version of the paper.
In our work we propose DETONAR, a novel intrusion detection system. DETONAR leverages traffic sniffing devices and traffic analysis technique to detect attacks in RPL networks. The proposed security mechanism builds a centralized security server allowing it to overcome drawbacks like RPL overhead and computational power requirements of IoT devices, common in competitor systems. DETONAR introduces a hybrid approach relying on the combination of anomaly-based detection and signature-based classification techniques. Combining these techniques DETONAR reaches reliable attack detection while maintaining low false positives.
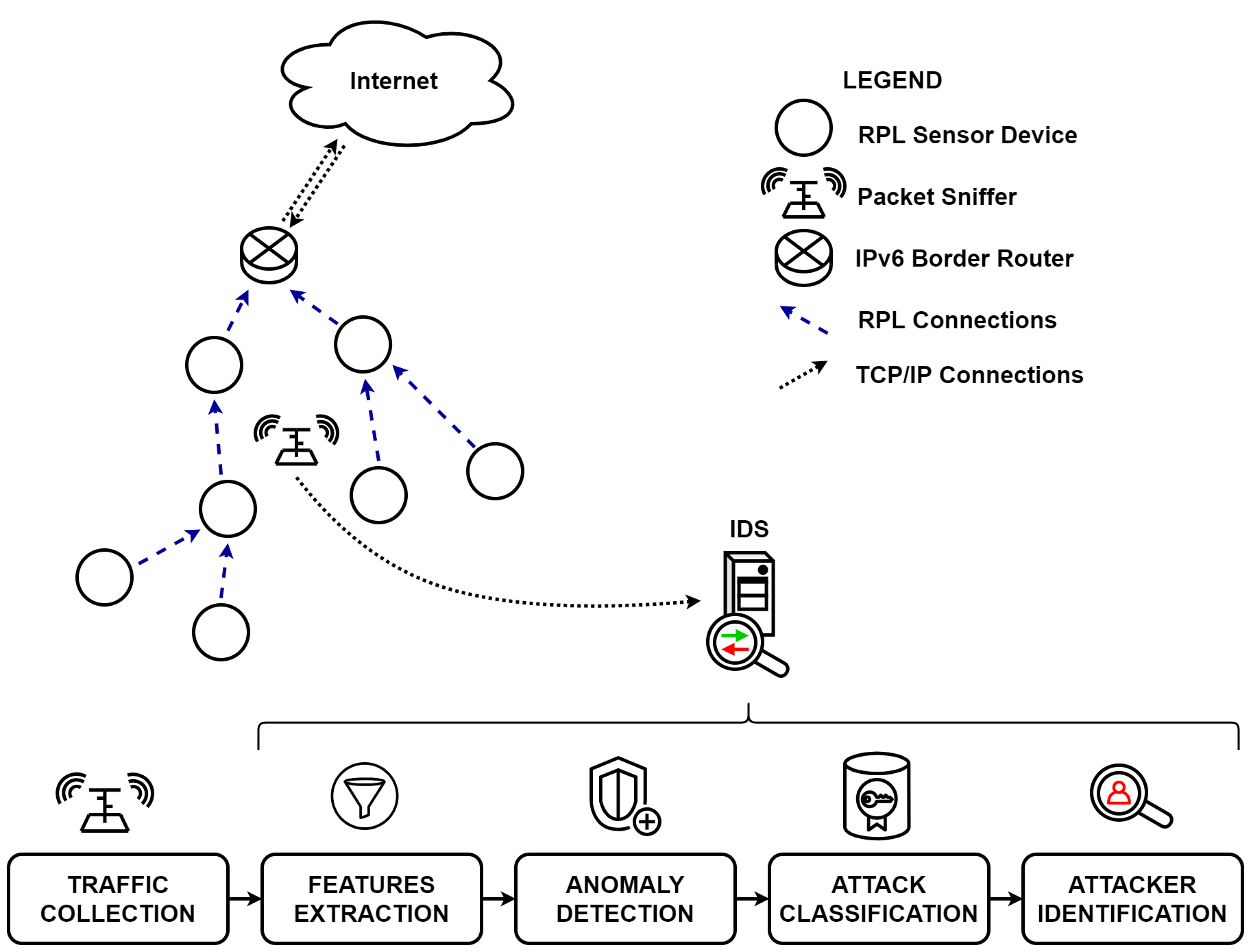
DETONAR’s pipeline, consisting of 5 steps: